

ゲームの全体的な構造を理解する
2023/12/23

osu! は .Net C# で書かれたリズムゲームです。そして私は osu! が大好きです。<3
なぜ逆コンパイルしようとしたのか?理由はカスタムクライアントです。有名なものとしては Auto+ や Akatsuki などがあります。
しかし、ソースコードは公開されていないため、ゲームのルートディレクトリにアクセスできません。
カスタマイズがどのように行われているのか、ただ興味があるだけです。
念のためお伝えしますが、osu! を再構築するつもりはありません。
ゲームの全体的な構造を理解することが目的なので、プログラムの改造やチート行為については書きません。
DnSpy などのツールを使って osu! のソースコードを復元しようとすると、識別子名が乱雑になり、すべての文字列定数が難読化された大きなバイナリファイルの中に隠されてしまいます。
読めませんね
これは難読化と呼ばれ、ソースコードを隠す方法の一つです。
ここで de4dot の出番です。
使用するには、ソースコードからビルドしてアプリケーションにロードするだけです。
osu! の最新バージョンを使用している場合、エラーが発生する可能性があります。2016 年から 2019 年半ばまでのバージョン、またはフォールバックバージョンの使用をお勧めします。
難読化方法はバージョンによって異なります。今回は Eazfuscator を使用して難読化を行いました。
バージョンに応じて ConfuserEx2 を使用しました。
成功すると、osu!-cleaned.exe という名前のアプリケーションが削除されます。
これを読み込むと、難読化されたバージョンとは異なり、クリーンなコードが表示されるはずです。
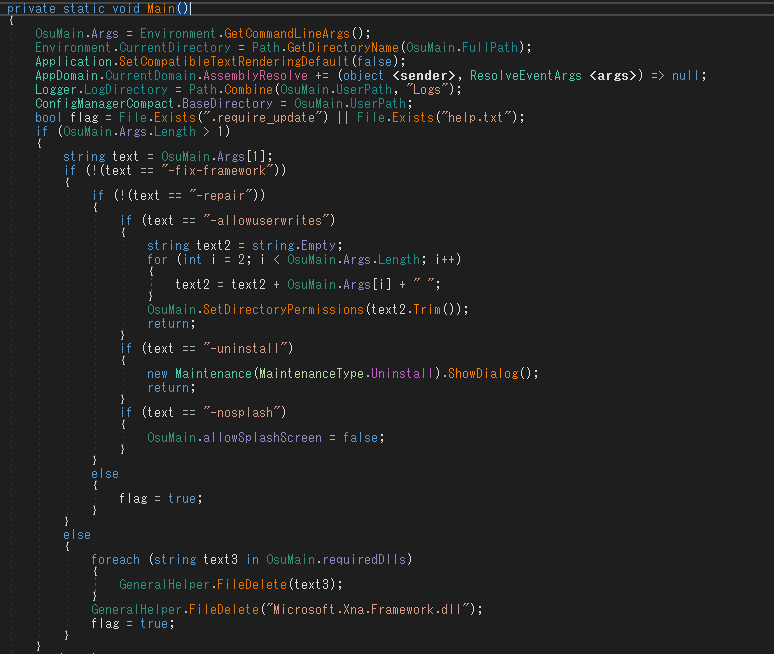
しかし、難読化が完全に解除されておらず、DnSpy機能を使用して難読化解除したコードをVS(Visual Studio)にエクスポートしようとしたところ、
プロジェクト全体で4,000件を超えるエラーが発生していました。バージョンによっては、難読化に使用されたものに応じて、1,000個から12,000個近くまで存在する可能性があります。